There are several ways to perform a connection from public internet to a private network (in this case – Home Labs), such as:
- Using remote software like: Chrome Remote Desktop, Ultraview, Teammviewer, AnyDesk => TL;DR 😉
- Nginx Proxy Manager
- Establish a vpn connection
- Cloudflare Tunnel
Nginx Proxy Manager
- Set up Dynamic DNS to automatically update the home IP for the domain name. We shall access through this domain name.
- Install
Nginx Proxy Manageron the server / virtual machine located in the home internal network to act as a Reverse Proxy for other network services. - Open port
80/443on the Router, redirect to the Nginx Proxy Manager server. - Create a Proxy Host on Nginx Proxy Manager, redirect to the corresponding network service that needs to be accessed from the outside.
Establish a vpn connection
We can access to the home network from internet via WireGuard VPN:
- Set up Dynamic DNS to automatically update the home IP for the domain name. We shall access through this domain name.
- Install
WireGuard VPNon a server / virtual machine in the internal network or set up WireGuard on the router if supported (Mikrotik, OpenWRT) - Open port
51820(UDP) on the Router, redirect to the WireGuard server - Create a Peer for the client to access from internet to the WireGuard VPN Server to the home labs.
Both of two methods have the advantage of being simple and quick to set up, but same disadvantages:
- Need to have a static IP, or need to set up Dynamic DNS in case the home network has a dynamic IP.
- Need to open ports on the main Router: 80 / 443 when using NPM or 51820 when using WireGuard VPN
Opening ports on the router always has many potential risks. In the worst case, outsiders can hack and access the internal network to steal personal information.
In addition, in many cases, the ISPs use Carrier-grade NAT, causing the home network have not Public IP and opening ports on the router is no longer meaningful, making both access methods via NPM or WireGuard VPN useless.
We can use another aproach – Cloudflare Tunnel with Cloudflare Zero Trust
Cloudflare Tunnel
Cloudflare Tunnel is a software that creates a secure network tunnel, connecting Cloudflare’s server system with servers in the internal network. All connections from the outside must go through Cloudflare’s censorship before being redirected to the internal network. We can hide our home network’s IP address, preventing network attacks from outside.
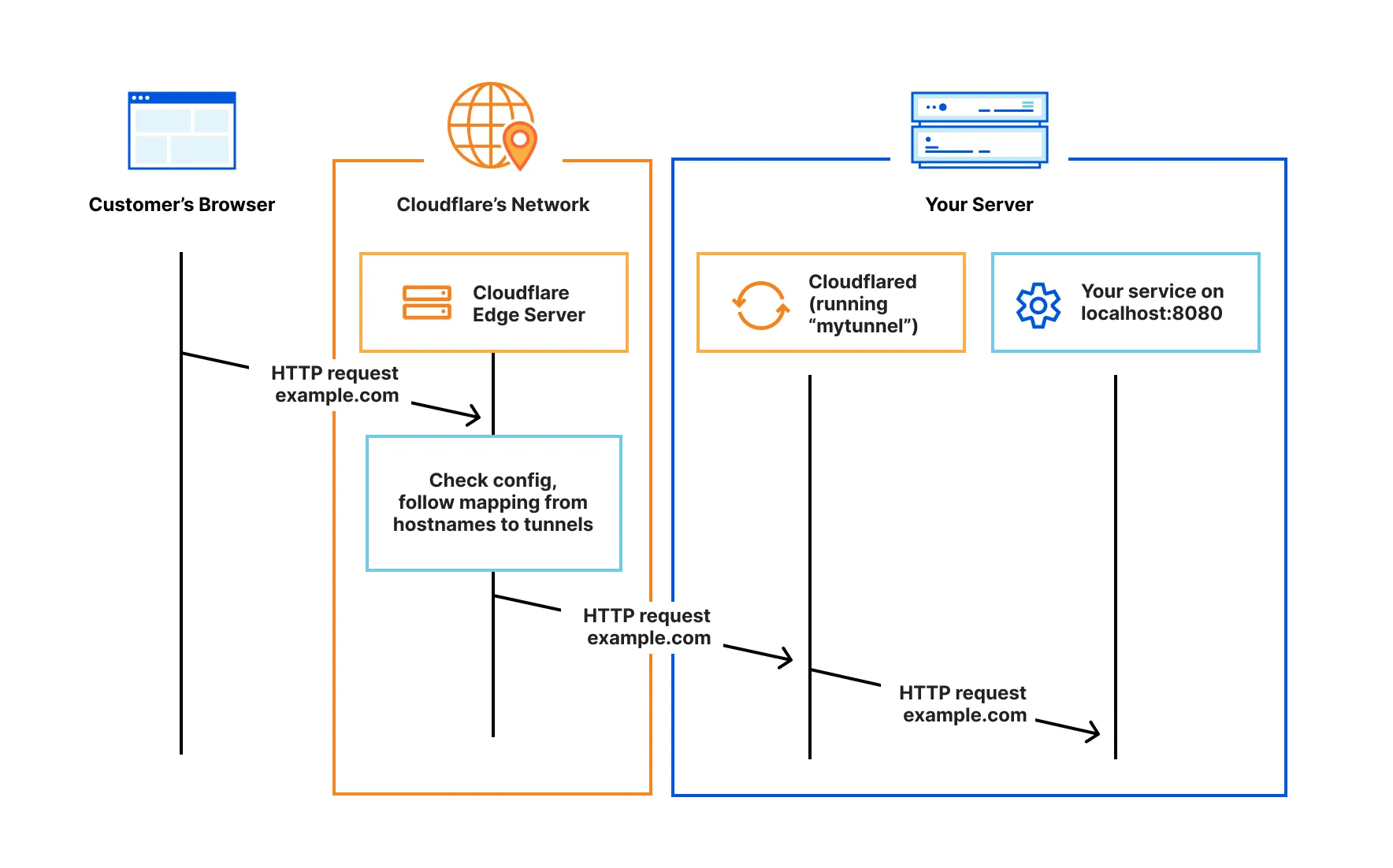
(Source: Cloudflare Zero Trust)
Advantages:
- Block direct access to the home network, no fear of IP address disclosure
- Take advantage of Tunnel’s Firewall and anti-DDoS system to protect the internal network system.
- No need to open ports, no need for static IP, no need to set up Dynamic DNS.
- Incorporate Cloudflare’s Zero Trust feature to authenticate all access to the internal network, optimizing security.
Disadvantages:
- Depends on Cloudflare’s system.
- Connection to Cloudflare’s system may lead to data risk.
Setting up
Register an account and point the cloudflare DNS to the domain.
Set up Cloudflare Tunnel by goto the Cloudflare Zero Trust at
https://one.dash.cloudflare.com/.
On first access, Cloudflare will ask to set up a team name (can be changed in the future if desired) -> Choose a Price -> Process on Purchase -> We can choose the Free plan.
1. Create Tunnel
- Go to
Networks->Tunnelsin the left menu. Click Create a tunnel to create a connection. - Select
Cloudflared-> Named the connection, and clickSave Tunnelto continue. -
Choose your environment with an architecture
-
Windows and x64 architecture:
-
Run the installer.
-
Open Command Prompt as Administrator.
-
Run the provied command in home labs server.
-
macOS:
- Download and install cloudflared via Homebrew:
brew install cloudflared
- Download and install cloudflared via Homebrew:
-
`
Note that keep the token in safe coz anyone with access to this token will be able to run the tunnel.
- After running on the server, return to the browser, you will see the Connectors section appear to notify that the connection is successful. The Origin IP section will show the IP address of the home network. Click Next to continue.
- Config the Route Traffic:
- Subdomain: select subdomain name.
- Domain: select domain name.
- Path: optional.
- Service: select connection type (HTTP, HTTPS, RDP,…) and internal IP address and corresponding port of the network service to be redirected.

Example: Config the RDP Tunnel
2. Set up Zero Trust security
According to the setup in the above step, anyone can create an connection to our home labs if they know the associated domain. To prevent unauthorized access, we shall set up additional authentication by creating additional Applications and Access groups.
Access groups: Navigate toAccess->Access groups, Add a group and Define group criteria Authentication Method – > OTPApplications: Navigate toAccess->Applications,
- Add an application with
Self-hosted - Application name: enter the application name
- Subdomain and domain: enter the information you used to set up the Public Hostname above
- The remaining items can be left as default
- Assign a group
- Policy name: Named some Policy name
- Configure rules -> Selector: Choose
Emailsand enter anemailto receive OTP. - In Setting, turn off the
Enable Binding Cookiefor connection non-HTTP like SSH and RDP.
- Add an application with
With this setting, every time you access the domain, the application will send an authentication code to the declared email.
3. Install cloudflared server-side daemon
We need to install cloudflared on the computer that we want to create an connection to the home lab.
4. Establish a RDP connection
- In Windows, Open Terminal and run:
cloudflared access rdp --hostname <your_host_name> --url rdp://localhost:33899 --log-level debug

- In macOS, Open Terminal anr run:
/opt/homebrew/opt/cloudflared/bin/cloudflared access rdp --hostname <your_host_name> --url rdp://localhost:33899 --log-level debug
The browser will automatically open the Cloudflare Access page and ask for an email verification. Enter email and go to the email box to get the otp code.

After entering the confirmation code in the email, the website will ask if you agree to connect. Select Approve.
After successful authentication, the Terminal will display the message ‘Waiting for login’. The RDP is promting for credential.

The connection is now established.
That’s all.
Ref:
- Connect to RDP server with cloudflared access
- ERR failed to connect to origin error="websocket: bad handshake"
-Nam Le,